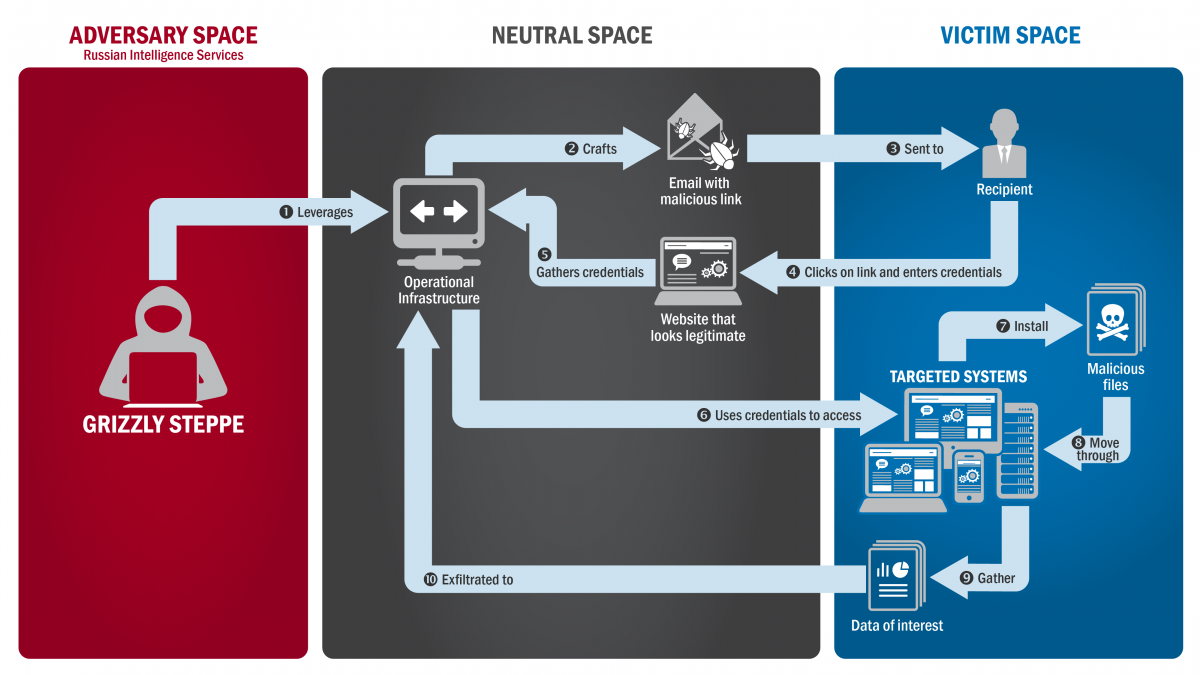
Microsoft President Brad Smith testified that a team of internal Microsoft security experts investigating the breach at the company estimated that the SolarWinds hack involved the work of “at least 1,000 engineers,” the sort of scale that would require a government’s commitment of people and money. Three top cyber leaders told lawmakers that old security models are no longer adequate for today’s IT environments.
By Brad D. Williams
NRO, NGA, CIA, DIA and NSA are the “standing members” of the new council, says its chairman David Gauthier of NGA.
By Theresa Hitchens
The NSA cannot mandate patching on its own, but the new Cybersecurity Maturity Model Certification (CMMC) allows the Pentagon to penalize companies in its supply chain that fail to adequately protect their networks.
By Kelsey Atherton
“We have widespread interest across DoD and other US Government Departments right now due to COVID,” John Woodruff, program manager for deviceONE at Air Force Research Laboratory, explained in an email to Breaking D.
By Theresa Hitchens
DISA will offer industry multiple contract opportunities to provide third-party tools to defend against malware and Zero Day attacks.
By Barry Rosenberg
“The average time it takes to discover a data breach is about six months,” said Hickey, a deputy assistant attorney general at the Justice Department specializing in cybersecurity and China. By the time you realize you’ve been hacked, it’s too late to “hack back” and shut down your attacker.
By Sydney J. Freedberg Jr.
The Air Force wants to develop information warfare capabilities to “deter malign activities from [the] information warfare level all the way up to conflict,” says Air Combat Command head Gen. Mike Holmes.
By Theresa Hitchens
The elevation of the cybersecurity mission to “its own Directorate raises its stature in NSA to a prominence that is absolutely needed,” says one former NSA official.
By Theresa Hitchens
China is copying malware the NSA has used against them. Is this preventable or is it an inherent weakness of cyber warfare?
By Theresa Hitchens
WASHINGTON: The entire US government — not just the Pentagon — needs to wake up to the intertwined threats of cyber warfare and political subversion, Army and National Security Agency officials say. It’ll take a major cultural change to get the whole of government to compete effectively in the grey zone between peace and war.…
By Sydney J. Freedberg Jr.
An adversary who has access to the dataset your AI trained on can figure out what its likely blind spots are, said Brian Sadler, a senior scientist at the Army Research Laboratory: “If I know your data, I can create ways to fake out your system.”
By Sydney J. Freedberg Jr.
CAPITOL HILL: The military’s new cyberspace force is working to overcome recruiting and retention shortfalls, training bottlenecks, and its dependence on the National Security Agency, officials told the Senate Armed Services Committee yesterday. These devils in the details are an inevitable part of standing up a new kind of force for a new kind of…
By Sydney J. Freedberg Jr.
WASHINGTON: Under relentless grilling from Democratic senators, the four-star officer who heads both Cyber Command and the NSA said the US government is “not doing enough” to prevent Russia from meddling in the 2018 elections. Could the US keep the Russians from interfering again? asked Sen. Claire McCaskill. “Yes,” Adm. Michael Rogers said at once.…
By Sydney J. Freedberg Jr.
WASHINGTON: The National Security Agency, which can go for 10 years without a contract protest, currently faces three, slowing the agency’s ability to issue new contracts. “We are sitting on three of them right now. Used to be you could go a decade without one, let alone sitting on three in one year,” Charlie Stein, of…
By Colin Clark